NextCloud installieren
Ordner erstellen
mkdir -p /opt/nextcloud/{database,app,daten}
Docker-Datei anlegen (/opt/nextcloud/Dockerfile)
FROM nextcloud
USER root
RUN apt update && apt install -y libmagickcore-6.q16-6-extra
Docker-Compose-Datei anlegen
/opt/nextcloud/docker-compose.yml
version: '3.3'
services:
nextcloud-db:
image: mariadb
container_name: nextcloud-db
command: --transaction-isolation=READ-COMMITTED --log-bin=ROW
restart: unless-stopped
volumes:
- /etc/localtime:/etc/localtime:ro
- /etc/timezone:/etc/timezone:ro
- /opt/nextcloud/database:/var/lib/mysql
environment:
- MYSQL_ROOT_PASSWORD=<SQL_root_Passwort>
- MYSQL_PASSWORD=<SQL_Benutzer_Passwort>
- MYSQL_DATABASE=nextcloud #Datenbank Name
- MYSQL_USER=nextcloud #SQL Nutzername
- MYSQL_INITDB_SKIP_TZINFO=1
networks:
- default
nextcloud-redis:
image: redis:alpine
container_name: nextcloud-redis
hostname: nextcloud-redis
networks:
- default
restart: unless-stopped
command: redis-server --requirepass <Redis_Passwort>
nextcloud-app:
build: .
container_name: nextcloud-app
ports:
- 127.0.0.1:8080:80
restart: unless-stopped
depends_on:
- nextcloud-db
- nextcloud-redis
environment:
REDIS_HOST: nextcloud-redis
REDIS_HOST_PASSWORD: <Redis_Passwort>
volumes:
- /opt/nextcloud/app:/var/www/html
- /opt/nextcloud/daten:/var/www/html/data
networks:
- default
collabora:
image: collabora/code
container_name: nextcloud-collabora
restart: unless-stopped
networks:
- default
ports:
- 127.0.0.1:9980:9980
environment:
- "domain=cloud\\.domain\\.tld"
- "dictionaries=de en"
- "username=<benutzername>"
- "password=<passwort>"
NC starten
cd /opt/nextcloud
docker-compose up -d
Seite aufrufen <ip-adresse>:8080 und Setup abschließen.
reverse Proxy anlegen
Zertifikat erstellen
certbot certonly --agree-tos --email admin@domain.tld --webroot -w /var/lib/letsencrypt/ -d cloud.domain.tld
Datei /etc/apache2/sites-available/cloud.domain.tld.conf
<VirtualHost *:80>
ServerName cloud.domain.tld
SSLEngine off
DocumentRoot /var/www/html/
RewriteEngine on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
</VirtualHost>
<VirtualHost *:443>
ServerName cloud.domain.tld
DocumentRoot /var/www/html/
SSLEngine on
SSLCertificateFile /etc/letsencrypt/live/cloud.domain.tld/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/cloud.domain.tld/privkey.pem
Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
RewriteEngine On
RewriteRule ^/\.well-known/carddav https://cloud.domain.tld/remote.php/dav/ [R=301,L]
RewriteRule ^/\.well-known/caldav https://cloud.domain.tld/remote.php/dav/ [R=301,L]
ProxyRequests Off
ProxyPreserveHost On
SSLProxyCheckPeerCN off
SSLProxyCheckPeerName off
<Location "/">
ProxyPass http://127.0.0.1:8080/
ProxyPassReverse http://127.0.0.1:8080/
</Location>
<Location "/.well-known/acme-challenge">
ProxyPass "!"
</Location>
CustomLog /var/log/apache2/cloud.domain.tld.log combined
ErrorLog /var/log/apache2/cloud.domain.tld.error.log
</VirtualHost>
Konfiguration aktivieren
a2ensite cloud.domain.tld.conf
systemctl reload apache2
Konfiguration anpassen
Datei /opt/nextcloud/app/config/config.php
...
'trusted_domains' =>.
array (
0 => '10.4.0.1:8080',
1 => 'cloud.domain.tld',
),
...
'overwrite.cli.url' => 'https://cloud.domain.tld',
...
'trusted_proxies' => '<IP-Adresse des Servers>',
'overwriteprotocol' => 'https',
'overwritehost' => 'cloud.domain.tld',
'default_phone_region' => 'DE',
'app.mail.verify-tls-peer' => false,
...
Container neu starten
docker-compose restart
Wenn beim Sicherheitscheck angezeigt wird, dass der Header X-Content-Type-Options nicht konfiguriert ist, kann das daran liegen, dass er doppelt gesetzt ist und muss in der NC-Konfiguration entfernt werden.
Datei /opt/nextcloud/app/.htaccess
...
#Header onsuccess unset X-Content-Type-Options
#Header always set X-Content-Type-Options "nosniff"
...
Cron Dienst anpassen
NC kennt mehrere Möglichkeiten, Hintergrund-Aufgaben zu erledigen. Da in einem Kontainer kein Dienst läuft, wird der cron-Dienst des Host-Servers verwendet.
In der ssh-Konsole als Benutzer root:
crontab -e
Befehl eintragen:
*/5 * * * * docker exec -t -u www-data nextcloud-app php -f /var/www/html/cron.php
NC-Einstellungen anpassen:
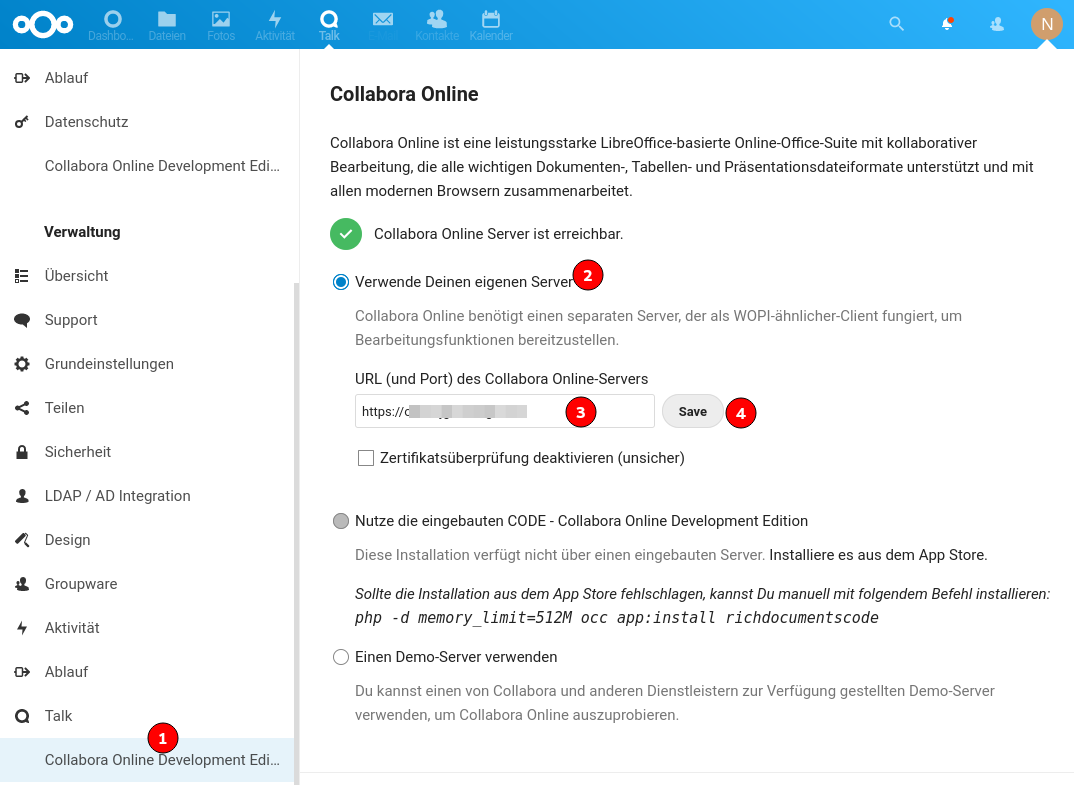
Colabora Office
Eigene Domain in Apache als Reverse Proxy anlegen
certbot certonly --agree-tos --email admin@domain.tld --webroot -w /var/lib/letsencrypt/ -d office.domain.tld
Datei /etc/apache2/sites-available/office.domain.tld.conf
<VirtualHost *:80>
ServerName office.domain.tld
SSLEngine off
DocumentRoot /var/www/html/
RewriteEngine on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
</VirtualHost>
<VirtualHost *:443>
ServerName office.domain.tld
# SSL configuration, you may want to take the easy route instead and use Lets Encrypt!
SSLEngine on
SSLCertificateFile /etc/letsencrypt/live/srv3.domain.tld/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/srv3.domain.tld/privkey.pem
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS
SSLHonorCipherOrder on
# Encoded slashes need to be allowed
AllowEncodedSlashes NoDecode
# Container uses a unique non-signed certificate
SSLProxyEngine On
SSLProxyVerify None
SSLProxyCheckPeerCN Off
SSLProxyCheckPeerName Off
# keep the host
ProxyPreserveHost On
# static html, js, images, etc. served from loolwsd
# loleaflet is the client part of LibreOffice Online
ProxyPass /loleaflet https://127.0.0.1:9980/loleaflet retry=0
ProxyPassReverse /loleaflet https://127.0.0.1:9980/loleaflet
# WOPI discovery URL
ProxyPass /hosting/discovery https://127.0.0.1:9980/hosting/discovery retry=0
ProxyPassReverse /hosting/discovery https://127.0.0.1:9980/hosting/discovery
# Main websocket
ProxyPassMatch "/lool/(.*)/ws$" wss://127.0.0.1:9980/lool/$1/ws nocanon
# Admin Console websocket
ProxyPass /lool/adminws wss://127.0.0.1:9980/lool/adminws
# Download as, Fullscreen presentation and Image upload operations
ProxyPass /lool https://127.0.0.1:9980/lool
ProxyPassReverse /lool https://127.0.0.1:9980/lool
# Endpoint with information about availability of various features
ProxyPass /hosting/capabilities https://127.0.0.1:9980/hosting/capabilities retry=0
ProxyPassReverse /hosting/capabilities https://127.0.0.1:9980/hosting/capabilities
CustomLog /var/log/apache2/office.domain.tld.log combined
ErrorLog /var/log/apache2/office.domain.tld.error.log
</VirtualHost>
Konfiguration aktivieren
a2ensite office.domain.tld.conf
a2enmod ssl proxy proxy_http proxy_wstunnel rewrite headers
systemctl restart apache2
In NC den eigenen Server eintragen:
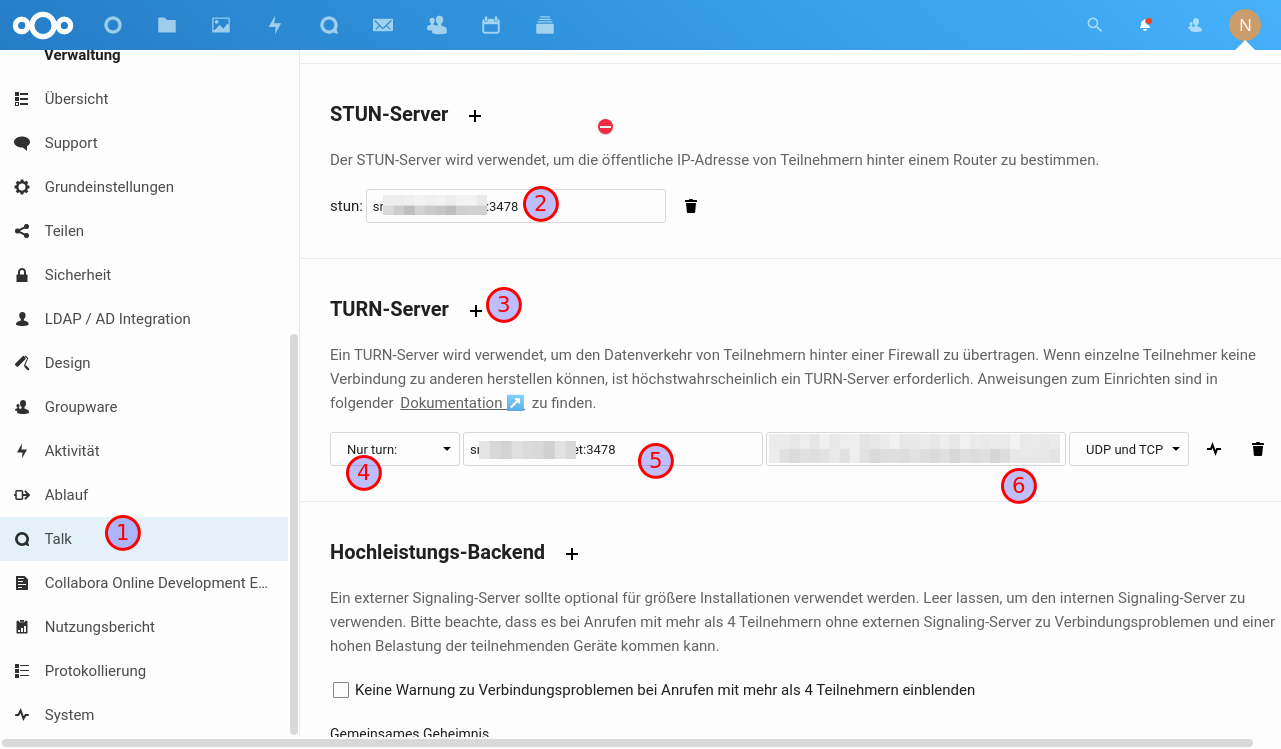
NextCloud Talk mit Signaling-Server
Turn-Server installieren
apt install coturn
In /etc/default/coturn aktivieren
TURNSERVER_ENABLED=1
Datei /etc/turnserver.conf anpassen
listening-port=3478
listening-ip=<IPv4-Adresse des Servers>
listening-ip=<IPv6-Adresse des Servers>
fingerprint
lt-cred-mech
use-auth-secret
static-auth-secret=<Secret>
realm=<FQDN des Servers>
total-quota=0
bps-capacity=0
no-tls
no-dtls
stale-nonce
no-loopback-peers
no-multicast-peers
proc-user=turnserver
proc-group=turnserver
Coturn-Server (neu) starten:
service coturn restart
Firewall anpassen
iptables -A INPUT -p tcp -m tcp --dport 3478 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp -m udp --dport 3478 -m state --state NEW,ESTABLISHED -j ACCEPT
ip6tables -A INPUT -p tcp -m tcp --dport 3478 -m state --state NEW,ESTABLISHED -j ACCEPT
ip6tables -A INPUT -p udp -m udp --dport 3478 -m state --state NEW,ESTABLISHED -j ACCEPT
netfilter-persistent save
NC-Einstellungen anpassen
Janus installieren
add-apt-repository ppa:fancycode/janus
apt update
apt install janus
Konfiguration anpassen:
Datei /etc/janus/janus.jcfg
nat: {
stun_server = "<server>"
stun_port = 3478
nice_debug = false
full_trickle = true
# ...
turn_rest_api_key = "<key>"
# ...
}
Mit dem Befehl openssl rand -hex 16 kann der <key> erzeugt werden.
Datei /etc/janus/janus.transport.http.jcfg
general: {
# ...
base_path = "/janus"
http = true
port = 8088
ip = 127.0.0.1
https = false
# ...
}
Datei /etc/janus/janus.transport.websockets.jcfg
general: {
# ...
ws = true
ws_port = 8188
ws_ip = 127.0.0.1
wss = false
# ...
}
Dienst (neu) starten:
systemctl restart janus
NATS einrichten
docker pull nats:latest
docker run --name=natsserver -d -p 127.0.0.1:4222:4222 -ti --restart=always nats:latest
Signaling-Server einrichten
apt install golang-go
cd /etc/
git clone https://github.com/strukturag/nextcloud-spreed-signaling.git
cd /etc/nextcloud-spreed-signaling
make build
Lokale Konfiguration erzeugen:
cd /etc/nextcloud-spreed-signaling
cp server.conf.in server.conf
Datei /etc/nextcloud-spreed-signaling/server.conf:
[http]
listen = 127.0.0.1:8086
[sessions]
hashkey = <session-hashkey>
blockkey = <session-blockkey>
[backend]
backends = backend1
[backend1]
url = <URL des Nextcloud-Servers>
secret = <Nextcloud-Secret>
[nats]
url = nats://localhost:4222
[mcu]
type = janus
url = ws://127.0.0.1:8188
[turn]
apikey = <API-Key von Janus (turn_rest_api_key)>
secret = <Secret von Coturn (static-auth-secret)>
Für <session-hashkey> kann openssl rand -hex 32 verwendet werden, <session-blockkey> darf nur 32 bytes haben und kann mit openssl rand -hex 16 gebildet werden.
Der Schlüssel <Nextcloud-Secret> kann ebenfalls mit openssl rand -hex 32 erzeugt werden und wird dann in NC eingetragen.
Benutzer und Dienst anlegen:
groupadd signaling
useradd --system --gid signaling --shell /bin/false --comment "Nextcloud Signaling" signaling
Datei /etc/systemd/system/nextcloud-signaling.service anlegen
[Unit]
Description=Nextcloud Talk signaling server
[Service]
ExecStart=/etc/nextcloud-spreed-signaling/bin/signaling --config /etc/nextcloud-spreed-signaling/server.conf
User=signaling
Group=signaling
Restart=on-failure
[Install]
WantedBy=multi-user.target
Dienst aktivieren und starten:
systemctl daemon-reload
systemctl enable nextcloud-signaling
systemctl start nextcloud-signaling
Dienste überprüfen:
Janus:
journalctl -u janus
Signaling-Server:
journalctl -u nextcloud-signaling
Apache-Proxy konfigurieren
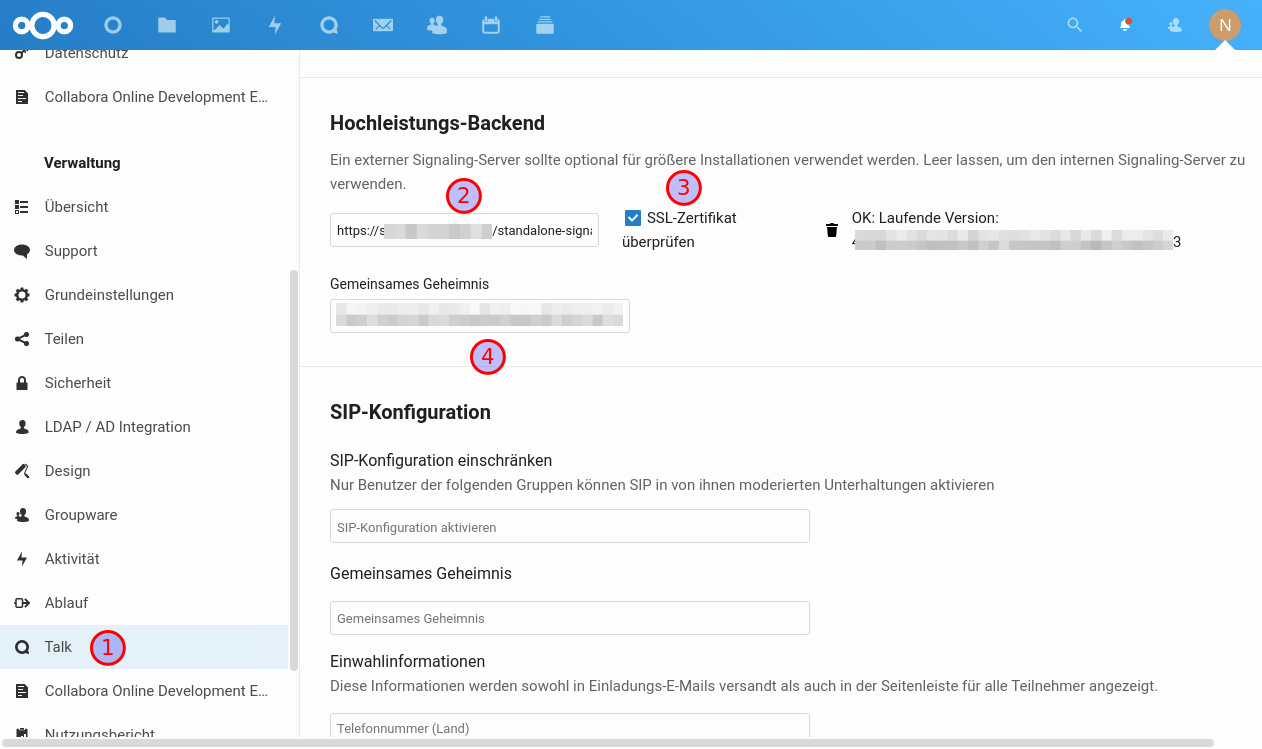
Entweder als eigene Subdomain, oder in die NC-Konfiguration integrieren:
RewriteEngine On
RewriteRule ^/standalone-signaling/spreed$ - [L]
RewriteRule ^/standalone-signaling/api/(.*) http://127.0.0.1:8086/api/$1 [L,P]
ProxyPass "/standalone-signaling/" "ws://127.0.0.1:8086/"
NC-Konfiguration anpassen:
Die URL wird mit https://<servername>/standalone-signaling angegeben, als "Gemeinsames Geheimnis" trägt man <Nextcloud-Secret> aus der Konfiguration des Signaling-Servers ein.